TL;DR:
There’s no such thing as a safe backdoor. “Lawful access” means building a weakness into encryption that governments promise only they’ll use. History shows us that every lawful backdoor eventually becomes a criminal’s front door.
Every few months the same idea resurfaces in political circles: “lawful access” to encrypted data. It’s usually wrapped in language about public safety, child protection, or counter-terrorism. The sales pitch is simple: give law enforcement a backdoor into encryption so they can catch the “bad guys.”
It sounds reasonable until you look at the technical reality. There is no such thing as a safe backdoor. The moment you create one, you’ve given every bad actor on the planet a target. A lawful backdoor is nothing more than a criminal’s front door.
Attackers don’t need to be clever once the door exists. They just need to find it, copy it, bribe someone for it, or wait for it to leak. And leak it will. Every time.
The Golden Key Fantasy
Governments love to talk about “golden keys” a special access mechanism that only authorised officials can use. But cryptography doesn’t work like a hotel lobby. You can’t hand out a spare master key and expect it to stay locked away in some drawer, secure or otherwise.
The Great Encryption Standoff
TL;DR France and Germany want backdoors into encrypted messaging apps for law enforcement. This would create security vulnerabilities that hackers could exploit. New cryptographic technologies like FHE and ZKP offer a middle ground, allowing data analysis while keeping everything encrypted, so governments can meet regulatory needs without compromising everyone's digital security.
History tells us exactly what happens:
The NSA’s EternalBlue exploit was designed for lawful use, and it ended up fuelling WannaCry and NotPetya ransomware attacks worldwide.
The Pegasus spyware toolkit was sold under the guise of counter-terrorism, then turned up in the phones of journalists, activists, and political opponents.
These were catastrophic breaches born out of “lawful” tools.
From Lawful to Open Access
Encryption is binary, it’s either secure or it’s not. Once you build a backdoor, the compromise is universal. You can’t design an algorithm that checks a badge and says, “Sorry, only lawful hackers today.”
Attackers don’t need to be clever once the door exists. They just need to find it, copy it, bribe someone for it, or wait for it to leak. And leak it will. Every time.
The Multiplication Effect
Backdoors don’t stay hidden, it’s impossible. They ripple through the ecosystem. When a cloud provider, messaging platform, or operating system is weakened, every company and every person using it inherits that vulnerability.
The Quiet Push for Encryption Backdoors in the EU — And Who’s Fighting It
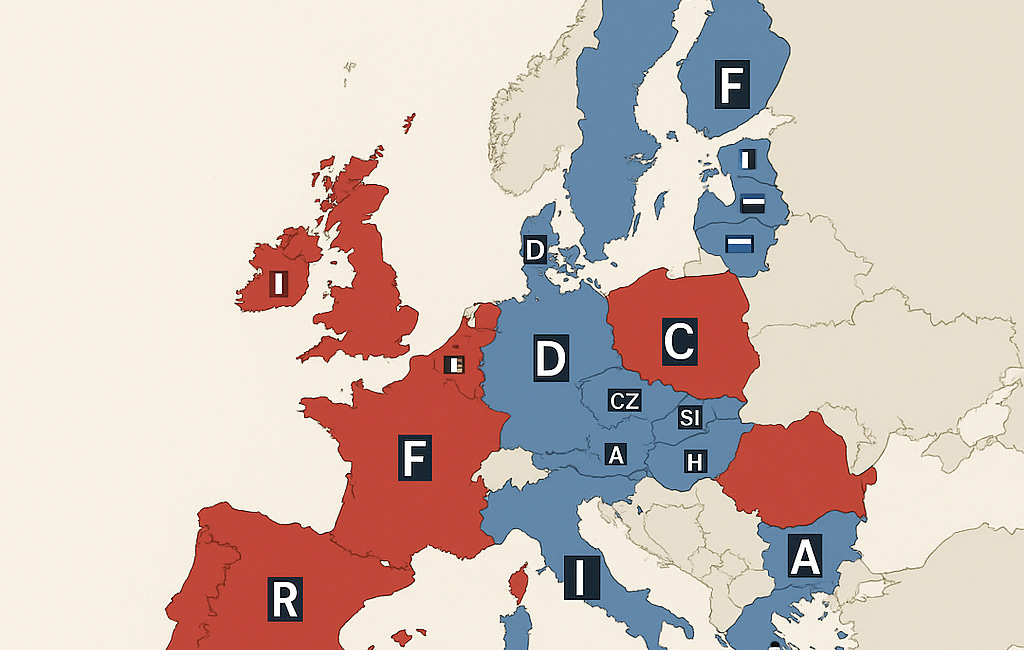
TL;DR: Several EU countries are quietly pushing to weaken encryption through laws like the CSA Regulation, which mandates client-side scanning. France, Ireland, and Belgium lead the charge for backdoors, while Germany, Austria, the Netherlands, Finland, and the Czech Republic resist. The fight over encryption is now playing out through obscure Council votes and vague “lawful access” language. What looks like child protection on paper risks becoming mass surveillance in practice. Czechia, where I’m relocating, remains cautiously privacy-aligned—for now.
For attackers, this is a gift. Instead of breaking into thousands of systems one by one, they go after the one backdoor key that opens them all. The maths of risk shifts instantly in their favour.
False Safety vs Real Security
Let’s be blunt: lawful backdoors don’t stop crime. Criminals adapt, switch to custom tools, or just build their own encrypted systems. The only people reliably exposed are businesses, citizens, and governments naïve enough to trust weakened infrastructure.
every lawful encryption backdoor is a criminal’s front door. And once it’s built, you don’t get to decide who walks through it.
If public safety is the real concern, there are better answers:
Zero-knowledge proofs that allow verification without exposing data.
Fully homomorphic encryption that lets investigators run computations on encrypted datasets without ever decrypting them.
Granular access control that ensures data can be used without being abused.
These aren’t science fiction. They’re technologies already in play that give regulators lawful outcomes without gutting security. This is what we do at PrivID. Our technology is based on FHE and ZKP. These systems are no longer the theoretical nice to haves for the future, they are here now, deployable and ready to use.
The Closing Reality
The Return of Lawful Access: Why the EU’s Encryption Roadmap Is a Trojan Horse
On April 1st, the European Commission released its five-year internal security strategy, ProtectEU. Buried among its various goals — from fighting terrorism to improving border control — lies a quiet but deeply troubling initiative: a “Technology Roadmap on Encryption.”
“Lawful access” is a euphemism for systemic vulnerability. It promises safety while guaranteeing exposure. It pretends that keys handed to governments won’t end up in the pockets of cybercriminals, hostile states, or the next ransomware gang.
The truth is simple: every lawful encryption backdoor is a criminal’s front door. And once it’s built, you don’t get to decide who walks through it.